“I am everywhere and I am nowhere. That’s the beauty of the Internet Age.” – Ai Weiwei
In part one of this series, we touched on the origins of blockchain and cryptocurrency technology, so let’s build on that today by exploring how it works. Don’t worry – the goal isn’t to be able to code the next cryptocurrency (and sorry to disappoint you, if that’s your aspiration). But, by approaching this in “bit-sized” pieces, we can better understand what is really happening behind the scenes and, hopefully, make the whole topic less daunting. Here we go!
Tissues vs. Kleenex
A blockchain can also be described as a distributed ledger technology (DLT). However, DLT is a more general term, defined as “a consensus of replicated, shared, and synchronized digital data geographically spread across multiple sites, countries, or institutions.” In this article that dives deeper into the differences between DLT and blockchain, it’s more simply phrased as “a database that exists across several locations or among multiple participants.” Easy enough.
As we covered in part one, the blockchain is (just like it sounds) a chain of blocks of information, but distributed ledgers don’t have that requirement. Thus, blockchain is a specific type of DLT – much like how Pepsi is a particular type of pop (aka soda, for some readers; and, for those who call all soda “Coke,” all hope may be lost). That may mean we’ll see other exciting DLT solutions that aren’t of the blockchain variety in the future. And, since blockchain is a more specific form of DLT, perhaps broader DLT solutions can overcome some blockchain-specific limitations (I’m saying this all very hypothetically).
Let’s Get Physical
As today’s quote alludes to, blockchain technology, like the internet, may conceptually be all around us, but it’s not something that exists in the physical world. That makes it (quite literally) more difficult to wrap our arms around. However, if we can imagine a blockchain transaction as a physical occurrence, that may help make it more relatable. In this respect, I found the below illustration of a blockchain transaction from Investopedia to be a helpful starting point. Note that this technically references Bitcoin, which we’ll spend more time on in a future Alt Blend, but don’t worry about that part for now:
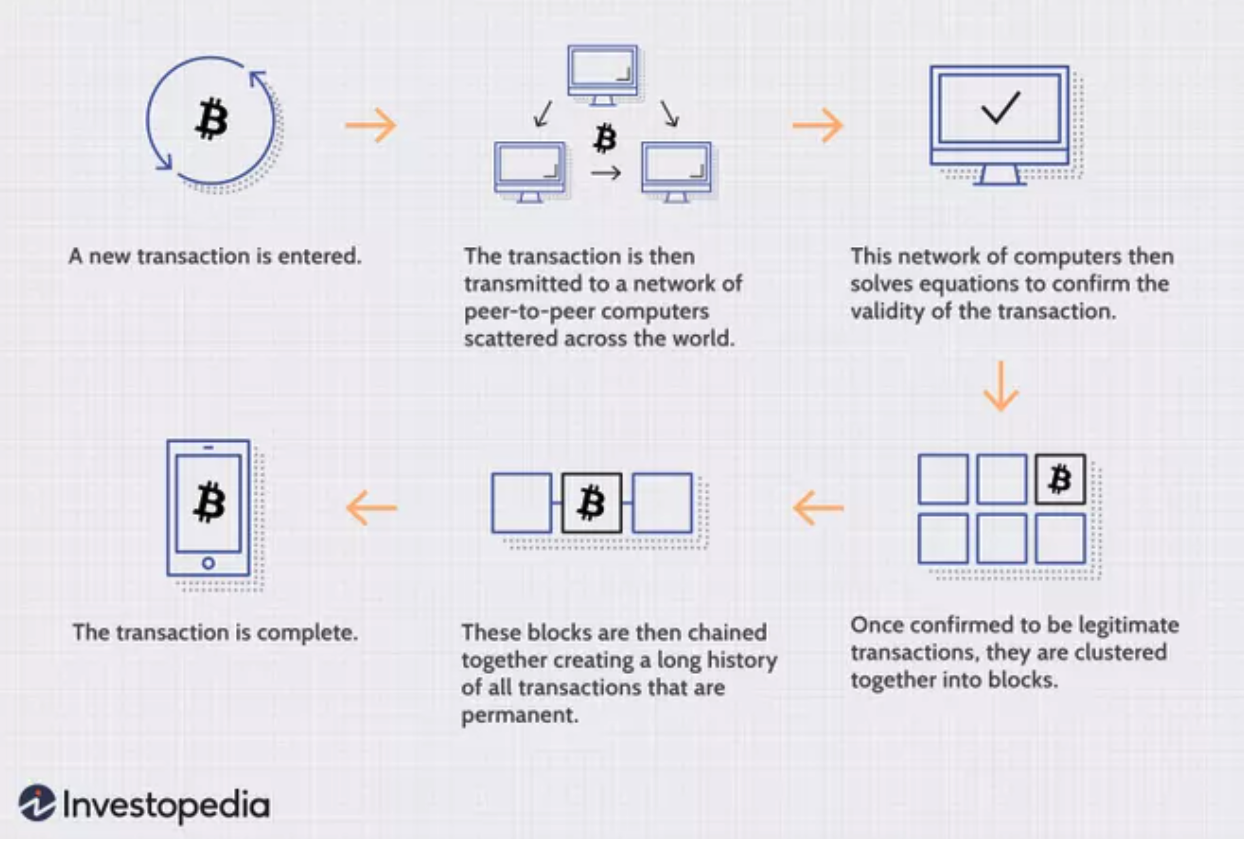
Now let’s put the above in a real-world context, appropriately using a Sopranos-style business transaction (yes, I live in New Jersey). The Gambino family is going to sell the Lucchese family a fleet of trucks, which they need for their new, legitimate (wink wink) catering business. The fleet costs $500k, to be paid in cash, and they’ll meet at the loading docks in Elizabeth, NJ to do the deal. In this new age of transparency, all five families now observe every transaction for verification and recordkeeping purposes. Here’s how it works:
Step 1: The Gambinos and Luccheses exchange the trucks for the money (akin to the transaction being entered on the network).
Step 2: The other three families – the Bonannos, Columbos, and Genoveses – are there to witness the whole thing and are provided with all of the related information, like make, model, years of trucks, serial numbers of the cash used, etc. (our “peer-to-peer network of computers”).
Step 3: The families then gather to count the money, inspect the trucks, and ensure the whole transaction checks out (aka “solving equations to confirm the validity of the transaction”).
Step 4: Unbeknownst to us as Sopranos viewers, Tony Soprano is a master etcher, and he’s now present for every transaction that takes place amongst the families. With his special skill set, they’ve devised a way to ensure no one can change the transaction records: when the transaction is deemed to be legitimate, Tony carefully etches the details onto a sheet of titanium, and once the sheet is full, then it’s sealed with an impenetrable layer of clear coat (this is the process of our transactions being “clustered together into blocks”).
Step 5: Each sealed titanium page is then added to an indestructible binder (obviously made of diamond), where none of the pages can ever be reordered, and none of the information can be changed, but any of the family members can review the complete transaction history – which they call “The Five-Family Blockchain” – at any time (the chaining together of our “blocks”), in case they fuggedaboutit.
And with that, we have a completed transaction and our perfectly believable, real-life blockchain example. Because the Five-Family Blockchain is just a process for reviewing, agreeing upon, and recording transactions, it can be used for virtually any type of transaction – not just exchanges of cash and trucks. Similarly, while the blockchain began with Bitcoin, the use cases have expanded far beyond either Bitcoin or cryptocurrencies since its advent.
Tales from the Crypt-ograph
We’ll expand on other use cases of blockchain in upcoming Alt Blend editions, but let’s close this current update by getting a better grasp on cryptography – a vital component of information security (aka protecting data from hackers). I encourage you to read this full Blockgeeks article, by Matthew Baggetta, for a more in-depth rundown of cryptography and its importance to blockchain, but I’ll give you the CliffsNotes® version, based on my interpretation (btw – did you know that CliffsNotes® still exists?).
When you hear about “encryption,” that’s cryptography at work. Conceptually, it’s like basic codes we did in elementary school: you can turn a phrase into different letters or numbers by creating a key to translate it into code. And your friend could use the same key to decipher the code back into the original message. That same idea holds, but encryption has become far more advanced as cryptography has evolved:
- Symmetric Cryptography: like an advanced version of our elementary school example – information gets encrypted using a key, it’s sent across the interwebs in coded form, and then the receiver uses the same key to decode it. If a hacker gets the key, that’s a problem. Also, as Bagetta mentions – how do you then send the key safely to the receiver?
- Asymmetric Cryptography: to address the above shortcomings, this uses a “system of public and private keys per user.” The public key is so a user can be identified as the proper recipient of information, but the sender’s private key is needed to encrypt the message, and only the recipient’s private key can be used to decrypt it on the other side.
- Cryptographic Hashing: with hashing, an algorithm is used to encode data, BUT there’s no decoding process. Instead, once the history is collectively agreed upon, that information is forever locked within a hash (a string of letters and numbers). The same data will always result in the same hash, so it’s clear whether or not the original data was altered in any way. Another exciting aspect is that large amounts of data can be compressed, as “hashes are always the same length, regardless of how long or extensive the [original] data is.”
# Blockchain
Tapping Wikipedia to help put this all together, “the blockchain is a growing list of records, called blocks, that are linked together using cryptography. Each block contains a cryptographic hash of the previous block, a timestamp, and transaction data (generally represented as a Merkle tree).”
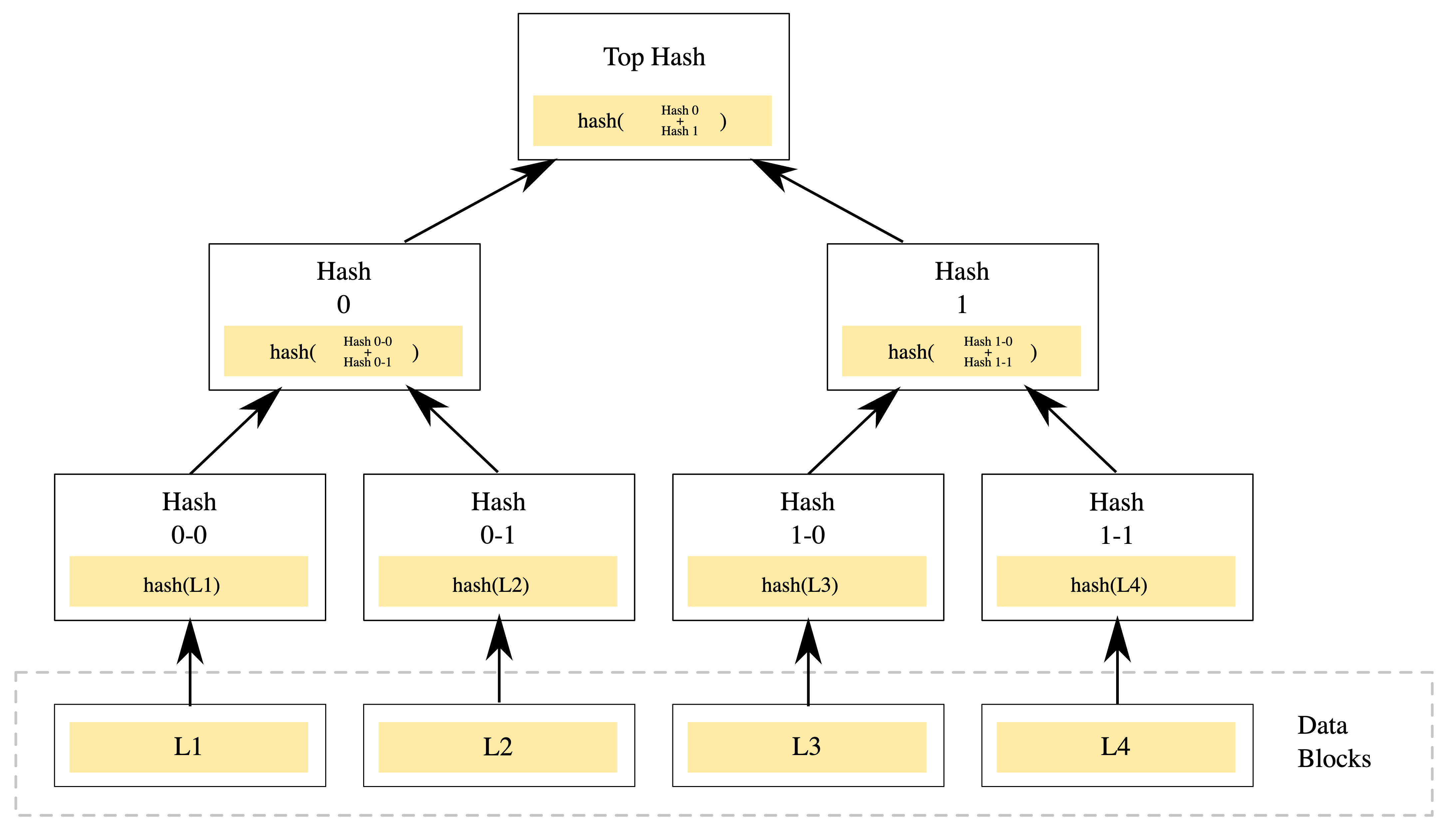
An example of a binary hash tree. Hashes 0-0 and 0-1 are the hash values of data blocks L1 and L2, respectively, and hash 0 is the hash of the concatenation of hashes 0-0 and 0–1 (Source: Wikipedia)
Hashing is what allows the various computers (also known as nodes) on the network to ensure data integrity of the blockchain by comparing hashes with what the original hash was supposed to be. Each block in the chain contains information about the previous block, so altering data retroactively would mean having to alter every subsequent block in the chain (activity that would not go unnoticed).
As Blockgeeks reminds us, combining DLT with the security, scalability, and reliability of cryptographic hashing is a #winning combination of features that makes blockchain so powerful, and THAT is why this technology may soon be “everywhere and nowhere.”
Until next time, this is the end of alt.Blend.
Thanks for reading,
Steve


